The Belgian cybersecurity sector is experiencing remarkable growth. According to a recent analysis by Agoria, revenue jumped 65% between 2021 and 2024, from €1.58 billion to €2.61 billion. The sector even forecasts a doubling by 2030, with annual growth of 15.9%.
These massive investments reflect a collective awareness. However, with an average of 275 cyberattacks per day in Belgium and one in four companies affected by 2024, a blind spot persists in many organizations: the custom application portfolio developed over the years.
Understanding the challenge of custom applications
Your business applications were carefully developed, often to meet specific needs that market solutions didn’t cover. It’s precisely because they are critical that they deserve special attention when it comes to security.
Let’s take a concrete example: a management application developed in 2015 for the public sector. At the time, it perfectly met security needs and standards. Today, the original developers have moved on, the frameworks used no longer receive updates, and security practices have progressed considerably. The application still works, but its attack surface has expanded without anyone noticing.
This situation is far from rare. It reflects a reality: the security landscape is evolving faster than our applications, and we need an approach to bridge this gap without rebuilding everything.
© 5th floor
A context that amplifies the urgency
“We recently saw the impact of a major cyberattack at our national airport, where criminals stole passenger data and held a business hostage.”

Eric Van Cangh
Leader of Cyber Made in Belgium at Agoria
The challenge is particularly acute for SMEs and the public sector. With 4,000 unfilled cybersecurity expert positions and a vacancy rate of 12.4% (compared to 5.3% in the rest of the IT sector), recruiting specialists is becoming extremely difficult. Meanwhile, 11% of cybersecurity services are provided to public administrations, which manage sensitive data while navigating budgetary constraints and limited resources.
The question then becomes: how can we strengthen the security of what we have partial control over, with limited resources and without rewriting everything?
L4F: a progressive modernization approach
It is to address this challenge that we at 5th floor have developed Legacy for the Future (L4F). Rather than a complete rewrite (which is costly and risky), we propose an iterative transformation based on three complementary pillars.
Auditing: establishing a clear vision
The first step is to understand exactly where we stand. Together, we analyze your application portfolio to identify not only technical vulnerabilities, but also their real impact on your business.
Concrètement, nous examinons :
External dependencies and their maintenance level
Current security practices vs. contemporary standards
Points of exposure to sensitive data
The level of documentation and knowledge available
The goal? To give you a precise map to prioritize your actions based on business risk, not just technical risk.
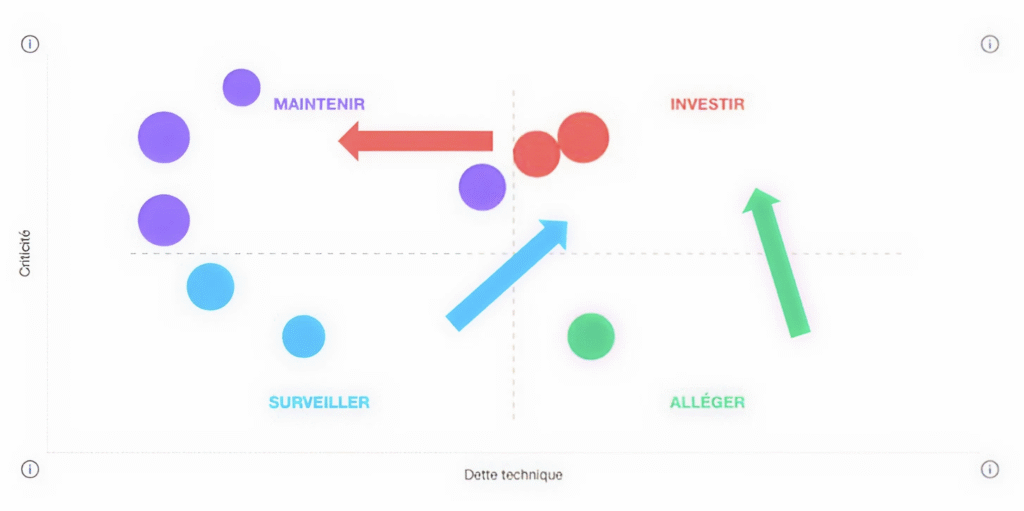
Example of a view of the L4F dashboard whose axes are the technical debt and the criticality linked to each app
Prioritise: act on what really matters
Not all vulnerabilities have the same impact. A flaw in an internal leave management application does not represent the same risk as exposing customer or user data. That’s why we work with you to develop an action plan that prioritizes interventions based on your value stream and business challenges.
This iterative approach allows for rapid results where they are most critical, while spreading the effort over time. Initial security improvements become visible within the first few weeks, without paralyzing your operations.
Mastering: building sustainable autonomy
Security is an ongoing process, not a one-time project. Therefore, developing the skills of your teams is at the heart of our approach. We work hand-in-hand with your employees: practical training, co-development, knowledge transfer, and documentation.
This iterative approach allows for rapid results where they are most critical, while spreading the effort over time. Initial security improvements become visible within the first few weeks, without paralyzing your operations.
"A few hundred graduates a year are not enough to close the gap. We urgently need greater cooperation with colleges, universities, and other educational institutions."

Saskia Van Uffelen
Manager Future Workforce at Agoria
In a market where 4,000 experts are missing, developing skills internally is becoming an essential resilience strategy.
The results observed
Our L4F methodology enables us to achieve tangible results on several projects:
- Reduce maintenance costs by up to 50%: fewer incidents, fewer emergency interventions, more predictability
- Improved stability and security: critical vulnerabilities addressed as a priority, measurable reduction of the attack surface
- Increased team autonomy: shared knowledge, ability to maintain and develop applications
- Budget freed up for innovation: reduction of technical debt allowing investment in new features
These benefits do not replace your overall cybersecurity strategy, but complement it by addressing an often overlooked angle.
Building a strengthened security posture together
With the industry growing at a rate of 15.9% annually and cyberattacks expected to increase by 165% by 2025, cybersecurity has become a critical business continuity issue. The good news? Your existing applications can become valuable assets if they’re given the attention they deserve.
L4F offers you a progressive and realistic transformation: identifying real risks, prioritizing high-impact actions, and building the autonomy of your teams. In a context of expertise shortages, this approach allows you to make concrete progress without relying solely on the external market.
Ready to strengthen the security of your application assets?
Let’s discuss your context and the transformation opportunities for your business applications. Our team can assist you with an initial risk analysis to identify your priorities. Let’s discuss your situation